Perhaps the Most Meaningful eDiscovery Business Confidence Survey Results Yet: eDiscovery Trends
The results are in from the ACEDS and Complex Discovery Summer 2016 eDiscovery Business Confidence Survey, which was conducted last month and (as was the case for the Winter and Spring surveys) the results are published on Rob Robinson’s terrific Complex Discovery site. Are individuals working in the eDiscovery ecosystem still as confident in the business as they were in the first and second quarters? Let’s see.
As always, Rob provides a complete breakdown of the latest survey results, which you can check out here. So, to avoid redundancy, I will focus on trends over the past three surveys (for the most part) to see how the responses have varied from quarter to quarter.
More Than Double the Respondents: This time, there were 168 total respondents to the survey, which is more than double the number of respondents as the Spring survey. In fact, there were twelve more respondents than the first two surveys combined. Obviously, sponsorship from ACEDS and promotion from EDRM, LTPI, Masters Conference, and Women in eDiscovery helped increase the number of respondents dramatically.
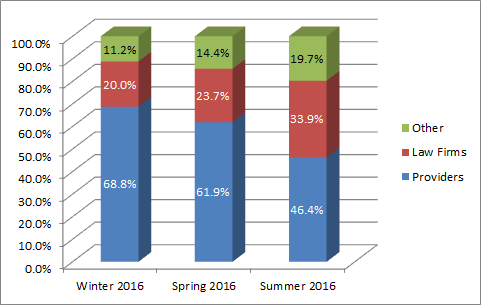
Providers Were No Longer the Majority Respondents: Of the types of respondents, 78 out of 168 were either Software and/or Services Provider (32.7%) or Consultancy (13.7%) for a total of only 46.4% of respondents as some sort of outsourced provider (down from 61.9% last time). Law firm respondents were in a strong second place with 33.9%. Even the percentage of other respondents (which includes Corporation and Governmental Entity respondents) was up from 11.7% (Winter) to 14.4% (Spring) to 19.7% this time. Here’s a graphical representation of the trend:
Less Respondents Consider Business to Be Good: Less than 48% (47.6%, to be exact) of respondents rated the current general business conditions for eDiscovery in their segment to be good, with 13.7% rating business conditions as bad. Last time, those numbers were 61.8% and 3.9% respectively. While this (and other) ratings reflect a dip, part of that could be attributable to the greater diversity in respondents (I would expect that providers would typically be more optimistic than the other groups). Then again, this could be a more realistic reflection of the industry as a whole. Here is the trend for the first three quarters:
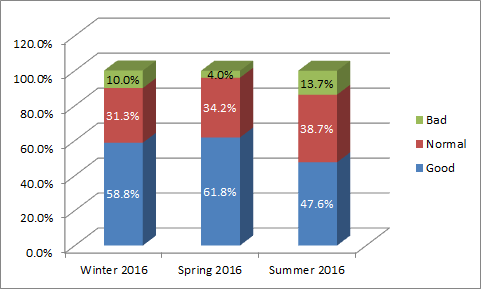
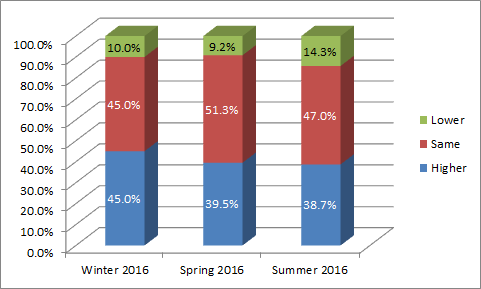
Almost Everyone Still Expects eDiscovery Business Conditions to be as Good or Better Six Months From Now: Almost all respondents (97.0%) expect business conditions will be in their segment to be the same or better six months from now (virtually changed from last quarter, though the “better” component dropped from 53.9% to 44.6%). That wasn’t reflected as much in the revenue and profit projections though, as 91.7% expected as good or better revenue and only 85.7% expected as good or better profits (“lower” reached a high of 14.3%). Here is the profits trend for the first three quarters:
Increasing Volumes of Data and Budgetary Constraints Continue to be Considered the Most Impactful to eDiscovery Business: Increasing Volumes of Data (28.6%) was actually considered to be the most impactful to the business of eDiscovery over the next six months, followed very closely by Budgetary Constraints (28.0%, one vote off). Lack of Personnel (14.3%) rose to third, Inadequate Technology (11.9%) rose considerably to fourth, Increasing Types of Data (10.1%) staying steady at fifth and Data Security (7.1%) dropping to dead last (it was second and third, respectively, in the first two surveys. The graph below illustrates the distribution across the past three surveys.
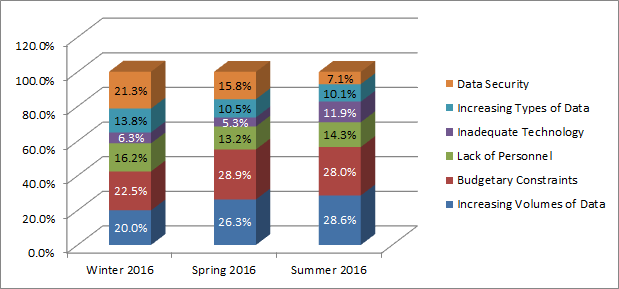
So, as the survey has become more diverse, the importance of Increasing Volumes of Data and Budgetary Constraints combined has risen from 42.5% in the Winter to 56.6% in the Summer. On the other hand, the importance of Data Security has dropped by two-thirds, from 21.3% in the Winter to 7.1% in the Summer (the number of respondents that selected data security – 12 – was exactly the same as last time even though the number of respondents more than doubled. Does that mean that providers place a higher priority on data security than law firms and other respondents? Maybe.
Level of Support in eDiscovery Business Reflects Considerable Diversity in Responses: A new question we’re covering here shows a virtual even split among type of respondents (based on role), with Executive Leadership and Operational Management tied at 34.5% of respondents each and Tactical Execution close behind at 31%. In the first two surveys, Executive Management was a majority of respondents with 56.3% and 55.6% respectively. So, this survey by far reflects the most balanced results based on role. It will be interesting to see if that trend continues in future surveys. Here’s that breakdown, quarter by quarter:
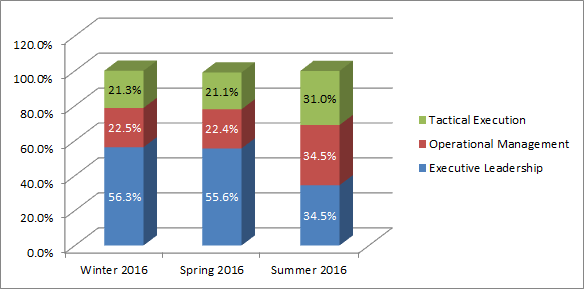
Rob has published the results on his site here, which shows responses to additional questions not referenced here. Check it out.
I’ll be participating in a panel discussion webinar moderated by Mary Mack of ACEDS with George Socha of EDRM also participating as a panelist where we will discuss these trends and others. Click here to register for that webinar.
So, what do you think? What’s your state of confidence in the business of eDiscovery? Please share any comments you might have or if you’d like to know more about a particular topic.
Disclaimer: The views represented herein are exclusively the views of the author, and do not necessarily represent the views held by CloudNine. eDiscovery Daily is made available by CloudNine solely for educational purposes to provide general information about general eDiscovery principles and not to provide specific legal advice applicable to any particular circumstance. eDiscovery Daily should not be used as a substitute for competent legal advice from a lawyer you have retained and who has agreed to represent you.