EDRM Announces Several Updates at Mid-Year Meeting – eDiscovery Trends

Last week, the Electronic Discovery Reference Model (EDRM) conducted its mid-year meeting to enable the working groups to meet and further accomplishments in each of the teams for the year. Having attended several of these meetings in the past, I’ve always found them to usually yield significant progress within the working groups, as well as providing a great opportunity for eDiscovery professionals to get together and talk shop. Based on the results of the meeting, EDRM issued an announcement with updates from several of their more active projects.
Here are the updates:
- Data Set: The Data Set project announced the launch of its new file upload utility. “The upload utility will allow us to develop a modern data set that more accurately represents the type of files that are commonly encountered in data processing,” said Eric Robi of Elluma Discovery, co-chair of the project with Michael Lappin of NUIX. The Data Set project also announced a soon-to-be-published “million file dataset” and an upcoming redacted version of the Enron data set, previously described on this blog here.
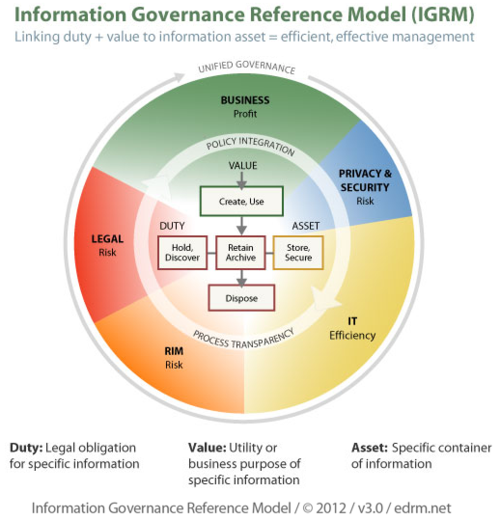
- Information Governance Reference Model (IGRM): The IGRM team announced that its updated model (IGRM v3) was recently published and presented at ARMA International’s 57th Annual Conference & Expo and the IAPP Privacy Academy 2012. As discussed on this blog just a couple of weeks ago, the updated version adds privacy and security as key stakeholders in the model.
- Jobs: The Jobs project continued development of the EDRM RACI (responsible, accountable, consulted, informed) Matrix, a tool designed to help hiring managers better understand the responsibilities associated with common e-discovery roles. RACI maps responsibilities to the EDRM framework so e-discovery duties associated can be assigned to the appropriate parties.
- Metrics: The Metrics project team refined the EDRM Metrics database, an anonymous set of e-discovery processing metrics derived from actual matters, which will include a CSV upload function to make it easier for vendors and law firms to anonymously submit data to the system. Having worked on the early stages of this project, my “hats off” to the team for the additional accomplishments.
- Search: The Search group announced that its EDRM Computer Assisted Review Reference Model (CARRM) soon will be available for public comment. The goal of CARRM is to demystify the predictive coding process and to allow for a common communication platform between vendors and end-users at each phase of the CAR process and it will be interesting to see the document that emerges from these efforts.
EDRM meets in person twice a year, in May for the annual meeting and October for the mid-year meeting, with regular working group phone calls scheduled throughout the year to keep the projects progressing. The next in person meeting is next year’s annual meeting, currently scheduled for May 7 thru 9, 2013. For more information about EDRM, click here. For information on joining EDRM, including fee information for participation, click here.
So, what do you think? Have you been following the activity of EDRM? Please share any comments you might have or if you’d like to know more about a particular topic.
Disclaimer: The views represented herein are exclusively the views of the author, and do not necessarily represent the views held by CloudNine Discovery. eDiscoveryDaily is made available by CloudNine Discovery solely for educational purposes to provide general information about general eDiscovery principles and not to provide specific legal advice applicable to any particular circumstance. eDiscoveryDaily should not be used as a substitute for competent legal advice from a lawyer you have retained and who has agreed to represent you.