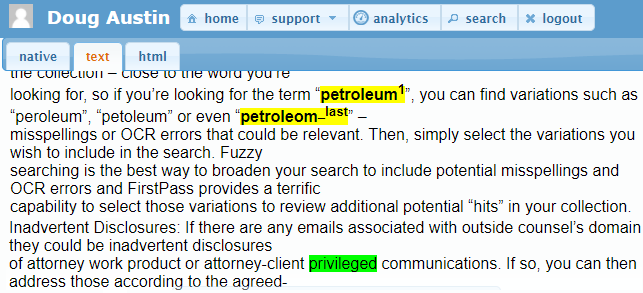
Only 53 Percent of Surveyed Security Officers Are Confident in Security of Data by Third Parties: Cybersecurity Trends
A recently issued report provides an interesting look at how Chief Information Security Officers (CISOs) and others responsible for security are addressing the challenges in today’s cybersecurity climate.
The report (The Shifting Cybersecurity Landscape: How CISOs and Security Leaders Are Managing Evolving Global Risks to Safeguard Data, by Ankura and Ari Kaplan Advisors), issued earlier this month, explores the roles of CISOs (chief information security officers), the adoption of cloud technology and how entities are auditing their vendors. Ankura partnered with Ari Kaplan Advisors and interviewed 30 industry leaders in August 2017, to detect how corporations are adapting to today’s evolving threat landscape. Most of these were large organizations (70 percent with over $1 billion in annual revenue, 80 percent with over 5,000 employees).
Interesting findings include:
- 97 percent of the respondents indicated they were evaluating security practices of their vendors, partners, law firms, and third parties that interact with their data. For 17 percent of them, regulatory requirements have driven that effort.
- However, only 53 percent said they were confident in the security of their data being managed by vendors, partners, and other third parties.
- 57 percent of the participants noted that their organizations are periodically involved in litigation or investigations that require them to transfer information to law firms and eDiscovery vendors, among others. 27 percent frequently need to do so.
- 87 percent of respondents were using third-party cloud providers to “host non-critical information” to save money and streamline business processes. 17 percent of the respondents noted that Office 365 is a common impetus for moving to the cloud.
- 77 percent of respondents advised that the scope of their managed security services includes incident response. And, for 63 percent, that support included onsite response. However, only 37 percent were confident that their managed services provider would provide a legally defensible investigation if they were the victim of a breach or other cyber incident.
- 80 percent of respondents reported having a Bring Your Own Device (BYOD) plan, though some noted that their plan is to prohibit personal devices. 63 percent believe that those gadgets contain company sensitive information.
GDPR is one significant regulatory requirement affecting security considerations, with one respondent stating that “GDPR will influence the way many companies appraise their partners, given the expansion of responsibilities for both data controllers and processors under the new privacy framework set for implementation in 2018.” Good thing we have a webcast on the topic tomorrow! :o)
The report, a 24 page PDF, chock full of other statistics and findings, is available here. As always, hat tip to Sharon Nelson of the Ride the Lightning blog for her coverage of the report.
So, what do you think? Do any of these numbers surprise you? Do you disagree with any of them? Please share any comments you might have or if you’d like to know more about a particular topic.
Sponsor: This blog is sponsored by CloudNine, which is a data and legal discovery technology company with proven expertise in simplifying and automating the discovery of data for audits, investigations, and litigation. Used by legal and business customers worldwide including more than 50 of the top 250 Am Law firms and many of the world’s leading corporations, CloudNine’s eDiscovery automation software and services help customers gain insight and intelligence on electronic data.
Disclaimer: The views represented herein are exclusively the views of the author, and do not necessarily represent the views held by CloudNine. eDiscovery Daily is made available by CloudNine solely for educational purposes to provide general information about general eDiscovery principles and not to provide specific legal advice applicable to any particular circumstance. eDiscovery Daily should not be used as a substitute for competent legal advice from a lawyer you have retained and who has agreed to represent you.