eDiscovery Best Practices: Could This Be the Most Expensive eDiscovery Mistake Ever?

Many of you have Android phones. I do, as well. As you may know, Android is Google’s operating system for phones and Android phones have become extraordinarily popular.
However, as noted in this Computerworld UK article, it may be a failure in searching that ironically may cost Google big time in its litigation with Oracle over the Android operating system.
Google is currently involved in a lawsuit with Oracle over license fees associated with Java. Oracle acquired Java when it purchased Sun Microsystems and many companies license Java. Java forms a critical part of Google’s Android operating system and Google has leveraged free Android to drive mobile phone users to their ecosystem and extremely profitable searches and advertising. Android has been so successful for Google that a loss to Oracle could result in billions of dollars in damages.
To cull down a typically large ESI population, Google turned to search technology to help identify potentially responsive and potentially privileged files. Unfortunately for Google, a key email was produced that could prove damaging to their case. The email was written by Google engineer Tim Lindholm a few weeks before Oracle filed suit against Google. With Oracle having threatened to sue Google for billions of dollars, Lindholm was instructed by Google executives to identify alternatives to Java for use in Android, presumably to strengthen their negotiating position.
"What we've actually been asked to do (by Larry and Sergey) is to investigate what technical alternatives exist to Java for Android and Chrome," the email reads in part, referring to Google co-founders Larry Page and Sergey Brin. "We've been over a bunch of these, and think they all suck. We conclude that we need to negotiate a license for Java under the terms we need."
Lindholm added the words “Attorney Work Product” and sent the email to Andy Rubin (Google’s top Android executive) and Google in-house attorney Ben Lee. Unfortunately, Lindholm’s computer saved nine drafts of the email while he was writing it – before he added the words and addressed the email to Lee. Because Lee's name and the words "attorney work product" weren't on the earlier drafts, they weren't picked up by the eDiscovery software as privileged documents, and they were sent off to Oracle's lawyers.
Oracle's lawyers read from the email at two hearings over the summer and Judge William Alsup of the U.S. District Court in Oakland, California, indicated to Google's lawyers that it might suggest willful infringement of Oracle's patents. Google filed a motion to "clawback" the email on the grounds it was "unintentionally produced privileged material." Naturally, Oracle objected, and after a three-month legal battle, Alsup refused last month to exclude the document at trial.
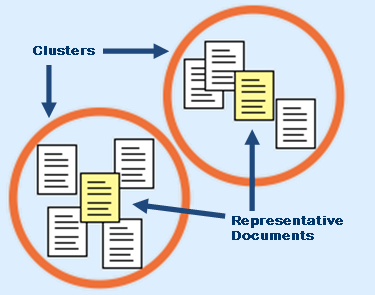
How did Google let such a crucial email slip through production? It’s difficult to say without fully knowing their methodology. Did they rely too much on technology to identify files for production without providing a full manual review of all files being produced? Or, did manual review (which can be far from perfect) let the email slip through as well? Conceivably, organizing the documents into clusters, based on similar content, might have grouped the unsent drafts with the identified “attorney work product” final version and helped to ensure that the drafts were classified as intended.
So, what do you think? Could this mistake cost Google billions? Please share any comments you might have or if you’d like to know more about a particular topic.