eDiscovery Daily Blog
How Long Will it Take to Crack Your Password?: Cybersecurity Trends
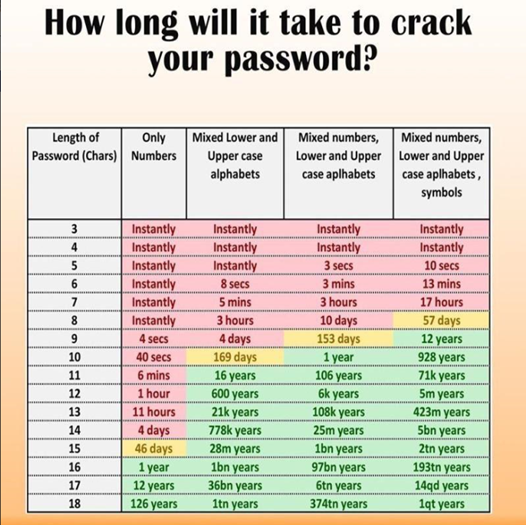
Have I mentioned lately how much I love an infographic? Well, I do. And this latest infographic that I have come across – from a Facebook friend who is also a colleague nonetheless – is a great one to note when considering your own passwords.
As you can see from the infographic above, the size and composition of your password could dramatically affect how long it takes to crack the password. For example:
- If you have a password that is numbers only, a password that is as much as eight numbers (that’s nearly 100 million number combinations) can still be cracked instantly;
- Even if that number only password is 14 numbers (that’s nearly 100 trillion number combinations), it only takes four days to crack a password even that size;
- Want to use all upper and lower case letters instead? That will help somewhat, but a five-letter password can still be cracked instantly;
- And a nine-letter password will still only take 4 days to crack;
- Want to mix numbers and upper and lower case letters? You’d better use more than seven characters or it will take no more than 3 hours to crack your password;
- Even with eight characters, it could still take as few as ten days;
- If you add in symbols, then a seven character password could still take less than a day;
- But, if you add an eighth character, that pushes the time up to 57 days. Add a ninth character? That pushes the time up to 12 years;
- But, notably, size does matter – when it comes to passwords and other things. ;o) An 18 number password still takes 126 years to crack, an 18 letter password takes a trillion years, an 18 number and letter password takes 374 trillion years and an 18 number, letter and symbol password takes 1 quintillion years!
Ain’t nobody got time for that!
Interesting! Of course, that’s one school of thought – here’s another, straight from the man who originally wrote password advice for the National Institute of Standards and Technology (NIST) and ultimately decided that advice was wrong. And, here’s a case from last year involving a criminal defendant who used a 64-character password to protect his device!
As I mentioned, I got this infographic from a Facebook friend – Michael Potters, who is also the CEO and Managing Partner of the Glenmont Group. It may be available in other places (not sure where it started), but I got it from Michael, so hat tip to him for the info!
So, what do you think? Does this change your thinking about password creation? Please share any comments you might have or if you’d like to know more about a particular topic.

Sponsor: This blog is sponsored by CloudNine, which is a data and legal discovery technology company with proven expertise in simplifying and automating the discovery of data for audits, investigations, and litigation. Used by legal and business customers worldwide including more than 50 of the top 250 Am Law firms and many of the world’s leading corporations, CloudNine’s eDiscovery automation software and services help customers gain insight and intelligence on electronic data.
Disclaimer: The views represented herein are exclusively the views of the author, and do not necessarily represent the views held by CloudNine. eDiscovery Daily is made available by CloudNine solely for educational purposes to provide general information about general eDiscovery principles and not to provide specific legal advice applicable to any particular circumstance. eDiscovery Daily should not be used as a substitute for competent legal advice from a lawyer you have retained and who has agreed to represent you.