eDiscovery Daily Blog
Want to Find Malware in Your Network Sooner? Listen to Your Network: Cybersecurity Best Practices
One of the most telling statistics about cybersecurity and data breaches that we covered during Wednesday’s webcast was from last year’s Verizon Data Breach Incident Report which said that almost 93 percent of breach compromise incidents occur within minutes, with 11 percent of those occurring within seconds. But, less than 25 percent of those breaches are discovered within days. Maybe your network traffic holds the key to detecting malware sooner.
According to this article in the Georgia Tech News Center by John Toon (with an assist by Sharon Nelson of the Ride the Lightning blog), security administrators could detect malware infections weeks or even months before they’re able to capture a sample of the invading malware by analyzing network traffic going to suspicious domains. Findings in a new study illustrate the need for new malware-independent detection strategies that will give network defenders the ability to identify network security breaches in a timelier manner.
As the article notes, the strategy would take advantage of the fact that malware invaders need to communicate with their command and control computers, creating network traffic that can be detected and analyzed. Having an earlier warning of developing malware infections could enable quicker responses and potentially reduce the impact of attacks, the study’s researchers say.
In the study, Manos Antonakakis, an assistant professor in the School of Electrical and Computer Engineering at the Georgia Institute of Technology, Graduate Research Assistant Chaz Lever and colleagues analyzed more than 5 billion network events from nearly five years of network traffic carried by a major U.S. internet service provider (ISP). They also studied domain name server (DNS) requests made by nearly 27 million malware samples, and examined the timing for the re-registration of expired domains – which often provide the launch sites for malware attacks.
The researchers had hoped that the registration of previously expired domain names might provide a warning of impending attacks, but found there was often a lag of months between when expired domains were re-registered and attacks from them began. The research required development of a filtering system to separate benign network traffic from malicious traffic in the ISP data. By studying malware-related network traffic seen by the ISPs prior to detection of the malware, the researchers were able to determine that malware signals were present weeks and even months before new malicious software was found.
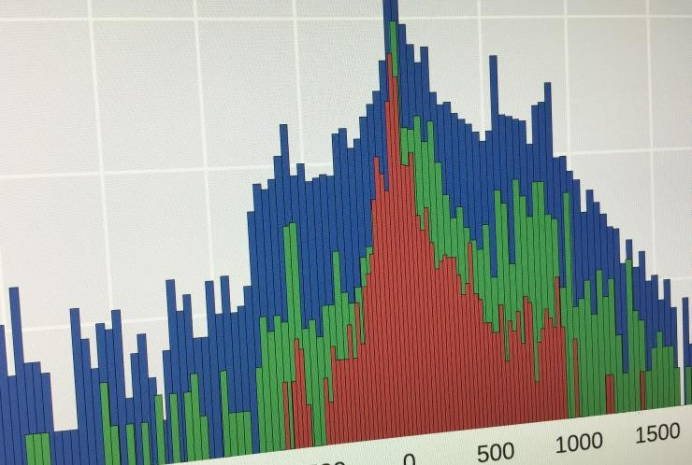
The chart above (courtesy of Georgia Tech) shows the time difference between when malware signals were detected in the network traffic of a major ISP and when the malware appeared on black lists.
In all, the researchers found more than 300,000 malware domains that were active for at least two weeks before the corresponding malware samples were identified and analyzed. The participants hope their study will lead to development of new strategies for defending computer networks.
So, what do you think? Could this become a breakthrough in defending against malware? Please share any comments you might have or if you’d like to know more about a particular topic.

Disclaimer: The views represented herein are exclusively the views of the author, and do not necessarily represent the views held by CloudNine. eDiscovery Daily is made available by CloudNine solely for educational purposes to provide general information about general eDiscovery principles and not to provide specific legal advice applicable to any particular circumstance. eDiscovery Daily should not be used as a substitute for competent legal advice from a lawyer you have retained and who has agreed to represent you.