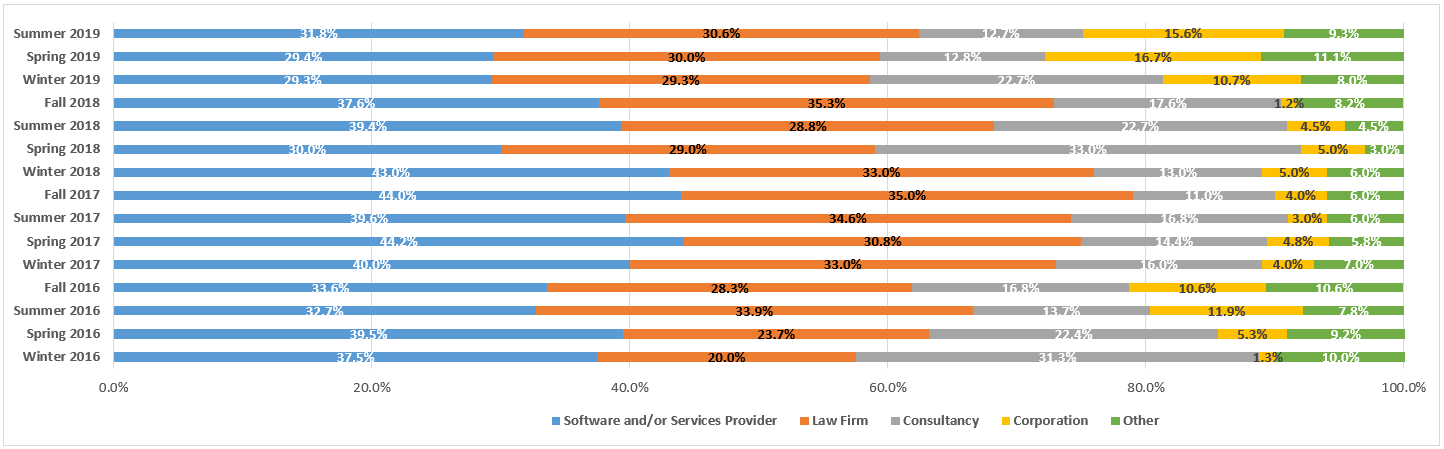
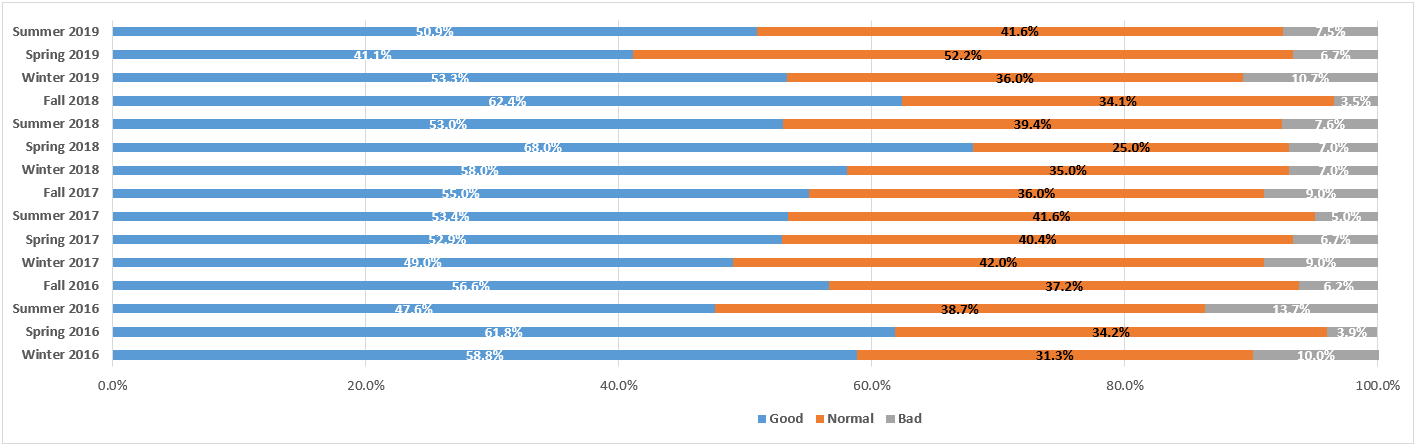
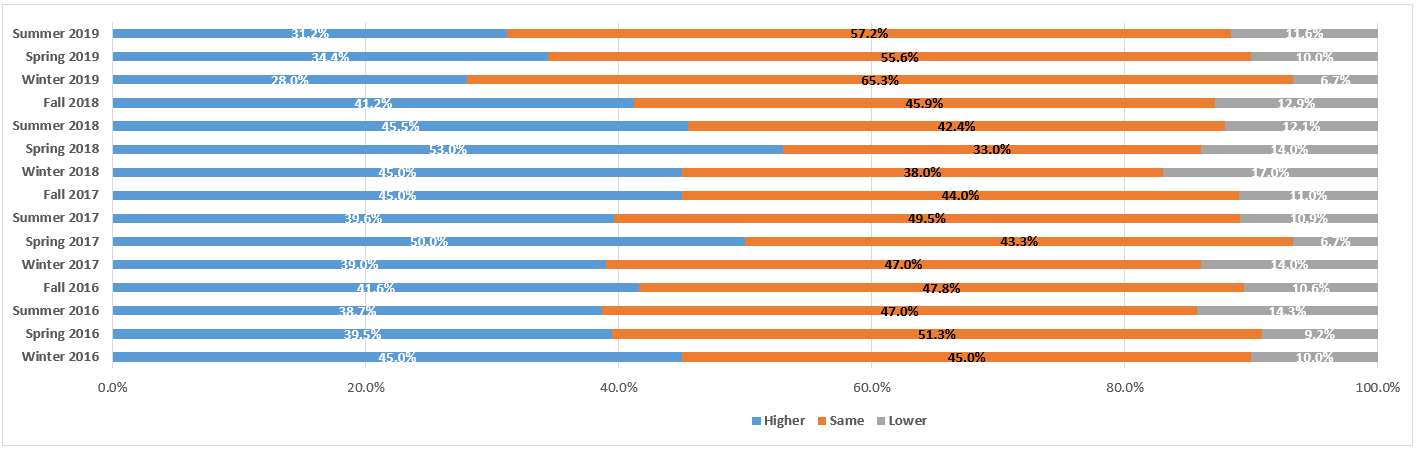
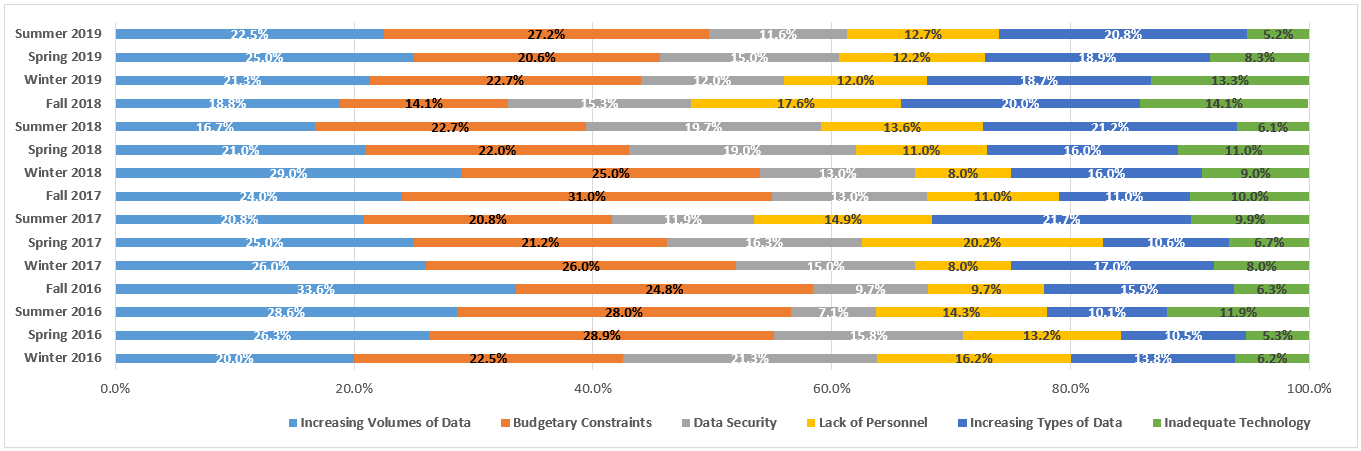
Court Recommends Finding of Intent to Deprive for Defendant’s Lost Text Messages: eDiscovery Case Law
Shark Week on the Discovery Channel continues, which means Case Week on the eDiscovery Channel (a.k.a., eDiscovery Daily) continues as well. Today’s case opinion comes from March and resulted in a different opinion for failure to preserve text messages than this case we covered last week. Enjoy!
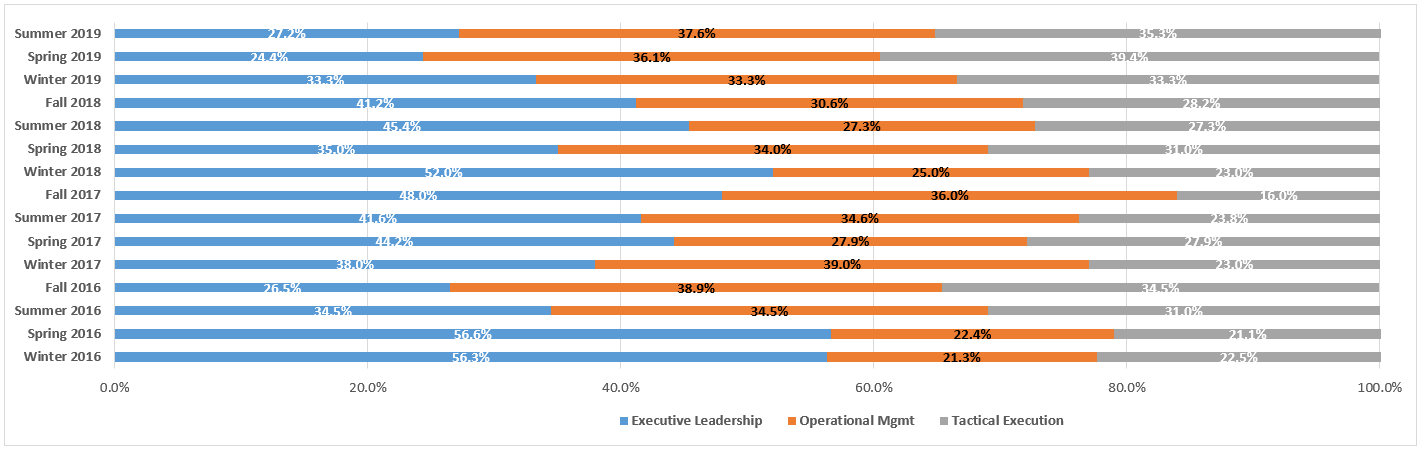
In NuVasive, Inc. v. Kormanis, No. 1:18CV282 (M.D.N.C. Mar. 13, 2019), North Carolina Magistrate Judge L. Patrick Auld recommended that, “because the record supports but does not compel a ‘finding that [Defendant Kormanis] acted with the intent to deprive [Plaintiff] of the [lost text messages’] use in the litigation, the Court submit that issue to the ‘jury, [with] the [C]ourt’s instruction[s] mak[ing] clear that the jury may infer from the loss of the [text messages] that [they were] unfavorable to [Defendant Kormanis] only if the jury first finds that [he] acted with the intent to deprive [Plaintiff] of the[ir] use in the litigation’”.
Case Background
In this case filed against a former employee over breach of contract for promoting and selling a competitor’s products within his former territory, the plaintiff notified Defendant Kormanis in March 2018 (through counsel) of its “concern[ ] that [his] new position with Alphatech will lead to … violation[s] of his contractual obligations with Ino[S]pine” and advised him “to refrain from the destruction of relevant evidence … including … texts … and to take steps to preserve all such information”. After the case was filed, the defendant wrote in response to the plaintiff’s production requests:
“As for text messages, due to space limitations on his iPhone, Defendant Kormanis only is able to keep data on his device from the previous 30 days. In order to comply with the litigation hold letter, Defendant Kormanis backs up his iPhone to his MacBook Air so that all messages are preserved. However, at this time, Defendant Kormanis has not been able to retrieve said messages from his personal devices. Once these communications are retrieved, they will be produced.” The defendant ultimately produced text messages on October 5, 2018, but there were no text messages produced prior to August 5, 2018. The defendant indicated that his vendor was unable to retrieve earlier text messages from his devices, but he declined to allow the plaintiff’s vendor to examine the devices.
In his subsequent affidavit and deposition, it became clear that the defendant failed to turn off the 30-day automatic delete function on his iPhone, leading to the loss of text messages after the defendant was advised of his duty to preserve them. Despite the defendant’s argument that “[t]he Court should deny [the instant] Motion because [Plaintiff] has failed to demonstrate that any of the allegedly spoliated text messages … would be relevant to this action”, Verizon records demonstrated that the defendant had regular text message communications with key parties in the case during that period where text messages were lost.
Judge’s Ruling
Judge Auld agreed with the plaintiff that “the relevance of these [text messages] is evident” and also stated: “Nor does any material dispute remain as to whether the loss of relevant text messages resulted from Defendant Kormanis’s failure to take reasonable steps to preserve them.” Judge Auld also noted that failure to follow the “simple steps” of suspending the auto-delete function on his phone and utilizing “relatively simple options to ensure that [his] text messages were backed up” was “sufficient to show that Defendant [Kormanis] acted unreasonably.”
As a result, Judge Auld granted the Plaintiff’s Motion for Imposition of Sanctions for Spoliation of Evidence in part. Judge Auld gave the plaintiff additional time to depose and subpoena text messages from a key Alphatech contact beyond the discovery deadline and ordered Defendant Kormanis to pay plaintiff’s fees/expenses associated with that effort and also all fees/expenses associated with filing, briefing and arguing the Instant Motion. He also issued the following recommendations:
“IT IS RECOMMENDED that the Court defer until trial the decision of whether other “serious measures are necessary to cure prejudice [from the loss of text messages], such as forbidding [Defendant Kormanis] from putting on certain evidence, permitting the parties to present evidence and argument to the jury regarding the loss of information, or giving the jury instructions to assist in its evaluation of such evidence or argument, other than instructions [that it may or must presume the lost text messages were unfavorable to Defendant Kormanis],” Fed. R. Civ. P. 37 advisory comm.’s note, 2015 amend., subdiv. (e)(1).
IT IS FURTHER RECOMMENDED that, because the record supports but does not compel a “finding that [Defendant Kormanis] acted with the intent to deprive [Plaintiff] of the [lost text messages’] use in the litigation,” Fed. R. Civ. P. 37(e)(2), the Court submit that issue to the “jury, [with] the [C]ourt’s instruction[s] mak[ing] clear that the jury may infer from the loss of the [text messages] that [they were] unfavorable to [Defendant Kormanis] only if the jury first finds that [he] acted with the intent to deprive [Plaintiff] of the[ir] use in the litigation,” Fed. R. Civ. P. 37 advisory comm.’s note, 2015 amend., subdiv. (e)(2).”
So, what do you think? Did the spoliation warrant a possible adverse inference instruction? Please let us know if any comments you might have or if you’d like to know more about a particular topic.

Case opinion link courtesy of eDiscovery Assistant.
Sponsor: This blog is sponsored by CloudNine, which is a data and legal discovery technology company with proven expertise in simplifying and automating the discovery of data for audits, investigations, and litigation. Used by legal and business customers worldwide including more than 50 of the top 250 Am Law firms and many of the world’s leading corporations, CloudNine’s eDiscovery automation software and services help customers gain insight and intelligence on electronic data.
Disclaimer: The views represented herein are exclusively the views of the author, and do not necessarily represent the views held by CloudNine. eDiscovery Daily is made available by CloudNine solely for educational purposes to provide general information about general eDiscovery principles and not to provide specific legal advice applicable to any particular circumstance. eDiscovery Daily should not be used as a substitute for competent legal advice from a lawyer you have retained and who has agreed to represent you.