Preparing for Litigation Before it Happens: eDiscovery Best Practices, Part Seven
Editor’s Note: Tom O’Connor is a nationally known consultant, speaker, and writer in the field of computerized litigation support systems. He has also been a great addition to our webinar program, participating with me on several recent webinars. Tom has also written several terrific informational overview series for CloudNine, including eDiscovery and the GDPR: Ready or Not, Here it Comes (which we covered as a webcast), Understanding eDiscovery in Criminal Cases (which we also covered as a webcast), ALSP – Not Just Your Daddy’s LPO, Why Is TAR Like a Bag of M&M’s?, eDiscovery for the Rest of Us (which we also covered as a webcast) and Litigate or Settle? Info You Need to Make Case Decisions (which is our next scheduled webcast on August 29th). Now, Tom has written another terrific overview regarding pre-litigation considerations titled Preparing for Litigation Before it Happens that we’re happy to share on the eDiscovery Daily blog. Enjoy! – Doug
Tom’s overview is split into seven(!) parts, so we’ll cover each part separately. Parts one, two and three were published last week, part four was published Monday, part five was published Tuesday and part six was published yesterday. Here’s the seventh and final part.
BTW, in addition to exhibiting at ILTACON in National Harbor, MD next week in booth 936, CloudNine will also host a happy hour on Tuesday, August 21 from 4:30 to 6:30pm ET at the National Harbor’s Public House (click here to register). Come and get to know CloudNine, your provider for LAW PreDiscovery®, Concordance® and the CloudNine™ SaaS platform! We want to see you!
Concluding Remarks
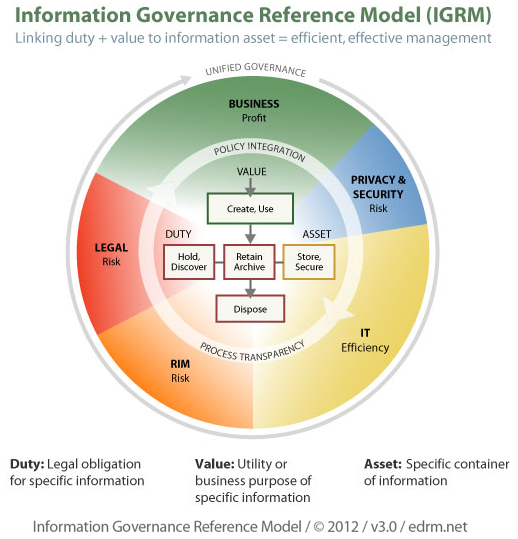
An IG strategy will depend entirely upon the business practice of your client and their various needs, including but not limited to proactive handling of eDiscovery matters for litigation.
ARMA suggests five main guidelines for building out the IG strategy that provide terrific guidance for any organization looking to implement or improve its IG program. They are:
1) Think big but start small: A good data governance process has three components: people, process and technology. Start by identifying and hiring the right people, then define a process, and finish by sourcing the technology to get the job done.
2) Build a business case: I had a client tell me once, “anyone can tell me what my problem is, Tom. You suggest solutions.” What are your goals? What are you trying to improve and how will the IG policy do it? Show an ROI to drive the change.
3) Metrics: You must be able to measure progress and display success to make your plan succeed. And since the plan will most likely take time to implement, use metrics to set milestones and measure progress.
4) Communicate: Regular and consistent communication is essential to show progress and correct problems that may arise during implementation. Include not just team members but all people in the organization with an emphasis on key players.
5) Get buy in: The project must become part of the business not something with a beginning and end date. You are making changes, not a product. Get buy in from everyone.
With an increased concentration on the two-fold concerns of privacy and security, IG has become more important than ever. These five guidelines can help your organization more efficiently and cost-effectively manage its data, enabling it to accomplish its organizational IG goals.
So, what do you think? Does your organization have a plan for preparing for litigation before it happens? As always, please share any comments you might have or if you’d like to know more about a particular topic.

Sponsor: This blog is sponsored by CloudNine, which is a data and legal discovery technology company with proven expertise in simplifying and automating the discovery of data for audits, investigations, and litigation. Used by legal and business customers worldwide including more than 50 of the top 250 Am Law firms and many of the world’s leading corporations, CloudNine’s eDiscovery automation software and services help customers gain insight and intelligence on electronic data.
Disclaimer: The views represented herein are exclusively the views of the author, and do not necessarily represent the views held by CloudNine. eDiscovery Daily is made available by CloudNine solely for educational purposes to provide general information about general eDiscovery principles and not to provide specific legal advice applicable to any particular circumstance. eDiscovery Daily should not be used as a substitute for competent legal advice from a lawyer you have retained and who has agreed to represent you.