Performing an Example Copy with Robocopy – eDiscovery Best Practices

Yesterday, we discussed the benefits of Robocopy, how to access it via the command line prompt (if you have Windows Vista or later) and how to get it (if you don’t). Today, we’re going to perform an example copy and take a look at the results.
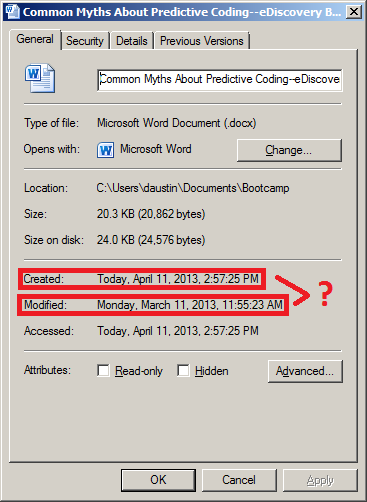
As you’ll recall, we discussed the pitfalls last week of using drag and drop for collecting files for eDiscovery and illustrated an example using a blog post that I wrote about a month ago in a Word document for the post Five Common Myths About Predictive Coding. If you followed the steps along with one of your own files, you noticed that the resulting file appeared to have been modified before it was created, which reflects spoliation of the metadata during the copy process. Let’s see how Robocopy handles that file copy.
I mentioned yesterday that Robocopy is a command line tool. If you’re really good at typing long commands at the command prompt without making a mistake, you can enter cmd in the ‘Search programs and files’ box from the Windows Start menu (‘Start’, then ‘Run’, for older versions on Windows) and that will open up a window with the command prompt. Feel free to “have at it”.
I actually use Excel as a Robocopy script builder – courtesy of CloudNine Discovery’s Vice President of Computer Forensics, Michael Heslop (thanks, Mikey!). The Excel workbook that I’m using takes user entered information regarding the custodian’s files to be copied and uses that to build a Robocopy statement that can then be executed at the command prompt. I have three script examples in the Excel file: 1) Script to copy all files/folders in a folder path, 2) Script to copy specific file extensions in a folder path, and 3) Script to copy one file in a folder path. It’s the third script example I’ll use here.
You’ll see below that I’ve highlighted the changes I’ve made to the single file copy script in the Excel spreadsheet, specifying the file name that I want to copy, the name of the custodian, the destination drive (in this case, the “E:” drive which references a connected external drive) and the path to be copied.
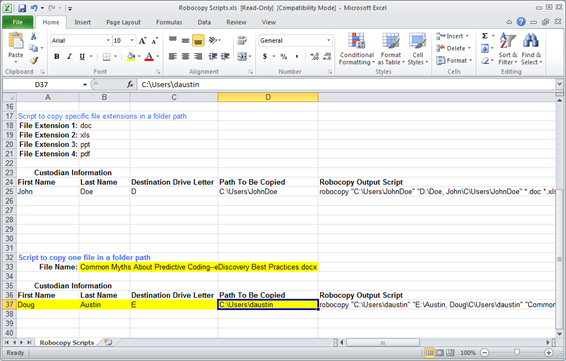
The resulting Robocopy statement created is as follows:
robocopy “C:Usersdaustin” “E:Austin, DougCUsersdaustin” “Common Myths About Predictive Coding–eDiscovery Best Practices.docx” /S /ZB /XJ /V /TEE /W:0 /R:0 /LOG+:”E:RobcopyLog-Austin,Doug.log”
This statement (that Michael created) takes the prompt information I’ve provided and uses it to build the Robocopy statement with desired copy and logging options. To see a list of available options for Robocopy, type robocopy /? at the command prompt.
I take the Robocopy statement and copy it, pasting it into an empty file in Notepad or Wordpad, then save it with a file name that contains a “.bat” extension (e.g., robocop1.bat, saved to my desktop). Then, simply double-click the file and it will open up a command window on the desktop and execute the statement.
Doing so put a copy of the file in the E:Austin, DougCUsersdaustinDocuments folder. It also created a log file at the root which documents every folder it checked and the one folder in which it found the file. Look at the properties of the copied file and you’ll see:
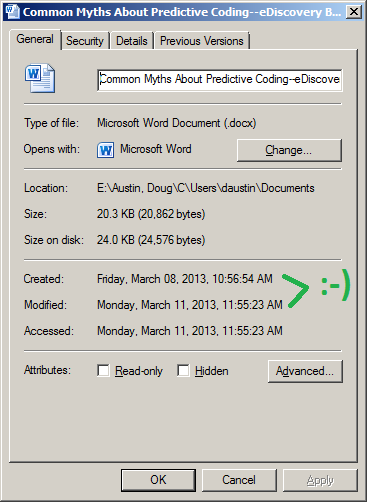
The Created date and the Accessed date reflect the original date and time when the file was created and last accessed. That’s what we want!
You can request a copy of my Excel Robocopy script builder by sending an email to me at daustin@cloudnincloudnine.comm and I’ll be happy to send it to you. It’s rudimentary, but it works!
So, what do you think? Have you used Robocopy as a mechanism for eDiscovery collection? Please share any comments you might have or if you’d like to know more about a particular topic.
Disclaimer: The views represented herein are exclusively the views of the author, and do not necessarily represent the views held by CloudNine Discovery. eDiscoveryDaily is made available by CloudNine Discovery solely for educational purposes to provide general information about general eDiscovery principles and not to provide specific legal advice applicable to any particular circumstance. eDiscoveryDaily should not be used as a substitute for competent legal advice from a lawyer you have retained and who has agreed to represent you.