Two Out of Three Companies Haven’t Reviewed Their Breach Preparedness Plans: Cybersecurity Trends
The singer Meat Loaf (real name Marvin Lee Aday) had a song once called Two Out of Three Ain’t Bad. Well, in this case, it is. According to a new study, many companies haven’t updated their data breach plans since developing them, report a lack of adequate employee training on data protection, and still haven’t figured out how to guard cloud services and mobile devices.
As reported by Legaltech® News (Two Out of Three Companies Haven’t Reviewed Their Breach Preparedness Plans, Study Says, written by Sue Reisinger), a study of global companies also found that just over half of professionals believed their C-suite executives knew the company’s plan to deal with a breach. The “Seventh Annual Study: Is Your Company Ready for a Big Data Breach?” was sponsored by Experian Data Breach Resolution and conducted by Ponemon Institute.
“I was surprised that two out of three respondents said they haven’t reviewed or updated their data breach preparedness plans,” said Michael Bruemmer, vice president of data breach resolution and consumer protection at Experian. “Preparedness plans can’t be a binder on a shelf that are not active and fluid plans. They should be reviewed and updated at least on a yearly basis.”
Bruemmer said a main takeaway from the report for general counsel is that “their clients are not preparing enough by practicing [data breach drills] and updating their response plans. They should work with clients to ensure this piece is a well-oiled machine.”
The study showed that 55% of respondents believed their C-suite executives knew the company’s plan to deal with a breach, but Bruemmer said the number should be higher. He recommended that general counsel make sure the CEO and C-suite “are knowledgeable and prepared for a data breach response. We have witnessed many leaders ill-equipped to handle the consumer response after a data breach.”
Here are some other notable study findings:
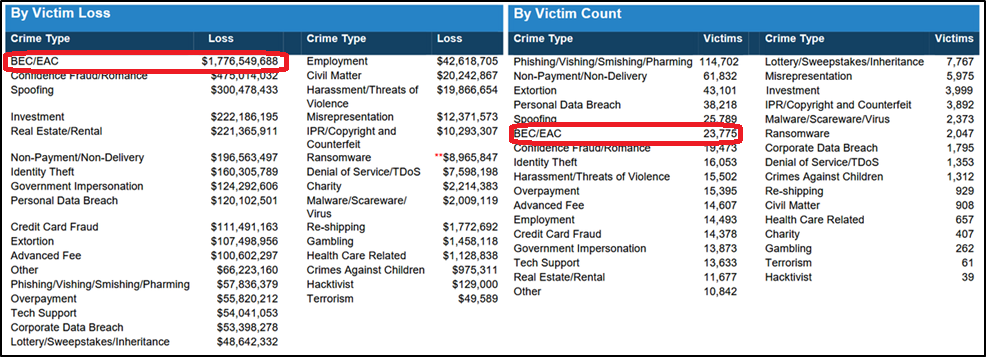
- About 36% of respondents reported their organization had a ransomware attack last year with only 20% feeling confident in their ability to deal with it. The average ransom was $6,128 and 68% of respondents say it was paid.
- Spear phishing attacks are pervasive, with 69% of respondents reporting one or more attacks and 67% saying the negative consequences of these attacks were very significant. Bruemmer called these threats “rudimentary at this point, and … a strong employee training program against these attacks [is] a must.”
- Some 68% of respondents said their company has put more resources toward security technologies to detect and respond quickly to a breach. Still data breaches are increasing, with significantly more organizations reporting data breaches than ever before. “Consequently, confidence levels among executives to thwart spear phishing and other common attacks have declined,” according to the report.
- More organizations at 54% report they have a high ability to comply with the European Union’s General Data Protection Regulation, compared with only 36% a year ago.
You can download a copy of the study from the Experian web site here.
So, what do you think? Are you surprised by any of these findings? As always, please share any comments you might have or if you’d like to know more about a particular topic.

Image Copyright © Page Six
Sponsor: This blog is sponsored by CloudNine, which is a data and legal discovery technology company with proven expertise in simplifying and automating the discovery of data for audits, investigations, and litigation. Used by legal and business customers worldwide including more than 50 of the top 250 Am Law firms and many of the world’s leading corporations, CloudNine’s eDiscovery automation software and services help customers gain insight and intelligence on electronic data.
Disclaimer: The views represented herein are exclusively the views of the author, and do not necessarily represent the views held by CloudNine. eDiscovery Daily is made available by CloudNine solely for educational purposes to provide general information about general eDiscovery principles and not to provide specific legal advice applicable to any particular circumstance. eDiscovery Daily should not be used as a substitute for competent legal advice from a lawyer you have retained and who has agreed to represent you.