Electronic Discovery on a First Date – eDiscovery Trends

Amy Bowser-Rollins in her excellent Litigation Support Guru blog raised an interesting question this week. How should we describe “electronic discovery” to someone who has never heard the term before or had very little exposure to the legal industry?
In her post Electronic Discovery on a First Date (you should especially check it out for the cute animation), she identifies various scenarios (a recent college graduate you just hired, curious or confused family members, your students, a stranger at a cocktail party) to answer the “what do you do for a living” question if you’re a litigation support provider. Some of us refer to this as the “elevator speech” in that you should be able to describe what you do in the time span of an elevator ride (no more than thirty seconds).
Amy tackles the question by breaking down “electronic discovery” into components, as follows:
- The practice of law
- Attorneys, more specifically litigators
- The discovery phase of a litigation matter, more specifically identifying, collecting, reviewing and producing documents
- Client documents, more specifically documents in electronic format
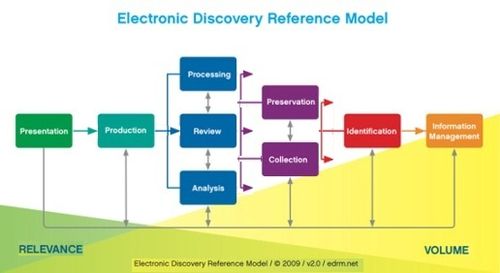
I might argue that “electronic discovery” sometimes also includes searching and reviewing the documents produced to you in litigation as well, not always just your client documents, but the components that Amy uses are certainly predominant for a litigation support professional and certainly fit the standard Electronic Discovery Reference Model (EDRM) that most use when they think of electronic discovery.
She then provides some examples of how she might use those components to answer the question. She uses the easiest document type for the layperson to identify with – email – to describe how she (or any typical litigation support person) helps litigators with the discovery process. I won’t steal her thunder – check out the link to her post above to see the examples that she proposed. Obviously, we all know that we work with more than just emails, so the example descriptions might be a bit oversimplified, but for the newbie, that’s probably the right way to start.
I can relate to Amy’s question with recent examples – explaining to my girlfriend on our first date what I do (a true “first date” scenario!) and explaining to a couple of recent entry-level candidates for positions at CloudNine Discovery. It’s a question that many of us wrestle with and a timely topic. Thanks, Amy!
So, what do you think? If you’re a litigation support or eDiscovery professional, how do you describe to others what you do? Please share any comments you might have or if you’d like to know more about a particular topic.
Disclaimer: The views represented herein are exclusively the views of the author, and do not necessarily represent the views held by CloudNine Discovery. eDiscoveryDaily is made available by CloudNine Discovery solely for educational purposes to provide general information about general eDiscovery principles and not to provide specific legal advice applicable to any particular circumstance. eDiscoveryDaily should not be used as a substitute for competent legal advice from a lawyer you have retained and who has agreed to represent you.