Preparing for Litigation Before it Happens: eDiscovery Best Practices, Part Three
Editor’s Note: Tom O’Connor is a nationally known consultant, speaker, and writer in the field of computerized litigation support systems. He has also been a great addition to our webinar program, participating with me on several recent webinars. Tom has also written several terrific informational overview series for CloudNine, including eDiscovery and the GDPR: Ready or Not, Here it Comes (which we covered as a webcast), Understanding eDiscovery in Criminal Cases (which we also covered as a webcast), ALSP – Not Just Your Daddy’s LPO, Why Is TAR Like a Bag of M&M’s?, eDiscovery for the Rest of Us (which we also covered as a webcast) and Litigate or Settle? Info You Need to Make Case Decisions (which is our next scheduled webcast on August 29th). Now, Tom has written another terrific overview regarding pre-litigation considerations titled Preparing for Litigation Before it Happens that we’re happy to share on the eDiscovery Daily blog. Enjoy! – Doug
Tom’s overview is split into seven(!) parts, so we’ll cover each part separately. Part one was published on Monday and part two was published on Wednesday. Here’s the third part.
BTW, in addition to exhibiting at ILTACON in National Harbor, MD later this month in booth 936, CloudNine will also host a happy hour on Tuesday, August 21 from 4:30 to 6:30pm ET at the National Harbor’s Public House (click here to register). Come and get to know CloudNine, your provider for LAW PreDiscovery®, Concordance® and the CloudNine™ SaaS platform! We want to see you!
General Principles for Information Governance
Assuming a company wanted to begin an IG initiative, are there any general principles to follow? The leading organization in this area is ARMA. Originally, ARMA was the acronym for the Association of Records Managers and Administrators. Over the years, the board of directors realized that records management had become a recognized and integral part of information governance, which is key to doing business. To reflect this change, they decided to discontinue using ARMA as an acronym and adopted “ARMA International” as a general descriptor of the association.
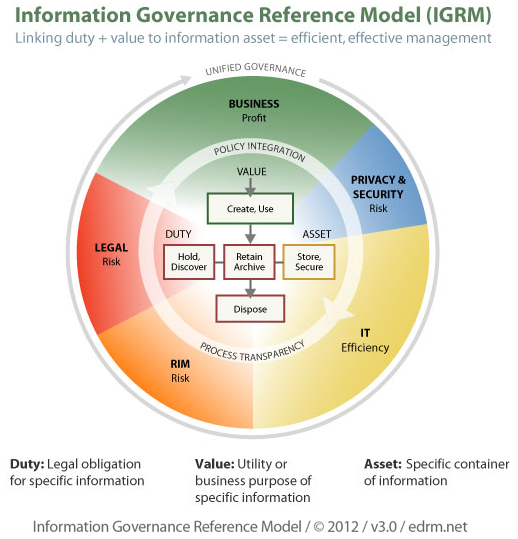
ARMA has 7 core principles it believes are the basis for any IG strategy. These Generally Accepted Recordkeeping Principles® (Principles) constitute a generally accepted global standard that identifies the critical hallmarks and a high-level framework of good practices for information governance – defined by ARMA International as a “strategic, cross-disciplinary framework composed of standards, processes, roles, and metrics that hold organizations and individuals accountable for the proper handling of information assets. Information governance helps organizations achieve business objectives, facilitates compliance with external requirements, and minimizes risk posed by sub-standard information-handling practices. Note: Information management is an essential building block of an information governance program.”
Published by ARMA International in 2009 and updated in 2017, the Principles are grounded in practical experience and based on extensive consideration and analysis of legal doctrine and information theory. They are meant to provide organizations with a standard of conduct for governing information and guidelines by which to judge that conduct and are, in fact, all contained with the eithht HIMA principles mentioned above.
Principle of Accountability: A senior executive (or a person of comparable authority) shall oversee the information governance program and delegate responsibility for information management to appropriate individuals.
Principle of Transparency: An organization’s business processes and activities, including its information governance program, shall be documented in an open and verifiable manner, and that documentation shall be available to all personnel and appropriate, interested parties.
Principle of Integrity: An information governance program shall be constructed so the information assets generated by or managed for the organization have a reasonable guarantee of authenticity and reliability.
Principle of Protection: An information governance program shall be constructed to ensure an appropriate level of protection to information assets that are private, confidential, privileged, secret, classified, essential to business continuity, or that otherwise require protection.
Principle of Compliance: An information governance program shall be constructed to comply with applicable laws, other binding authorities, and the organization’s policies. Principle of Availability: An organization shall maintain its information assets in a manner that ensures their timely, efficient, and accurate retrieval.
Principle of Retention: An organization shall maintain its information assets for an appropriate time, taking into account its legal, regulatory, fiscal, operational, and historical requirements.
Principle of Disposition: An organization shall provide secure and appropriate disposition for information assets no longer required to be maintained, in compliance with applicable laws and the organization’s policies.
We’ll publish Part 4 – Who Uses Information Governance? – next Monday.
So, what do you think? Does your organization have a plan for preparing for litigation before it happens? As always, please share any comments you might have or if you’d like to know more about a particular topic.
Sponsor: This blog is sponsored by CloudNine, which is a data and legal discovery technology company with proven expertise in simplifying and automating the discovery of data for audits, investigations, and litigation. Used by legal and business customers worldwide including more than 50 of the top 250 Am Law firms and many of the world’s leading corporations, CloudNine’s eDiscovery automation software and services help customers gain insight and intelligence on electronic data.
Disclaimer: The views represented herein are exclusively the views of the author, and do not necessarily represent the views held by CloudNine. eDiscovery Daily is made available by CloudNine solely for educational purposes to provide general information about general eDiscovery principles and not to provide specific legal advice applicable to any particular circumstance. eDiscovery Daily should not be used as a substitute for competent legal advice from a lawyer you have retained and who has agreed to represent you.