The digital age has had a major impact on more than just how we occupy our free time. It’s also changed the way we review and process legal data.
Lawyers and paralegals handle much more than the physical evidence of discovery. Most law firms sift through unprecedented volumes of evidence that come with the digital age.
When Data Volumes Exceed Capacity: Controlling The Ever Growing Amount of Data
Legal service providers (LSPs) review and process massive sets of complex and diverse digital content oftentimes, in the terabytes. For context, consider this comparison of data:
- 1 MB = a 400-page book
- 1 GB = over a thousand 400-page books
- 1 TB = more than a million 400-page books
Faced with this overwhelming volume of data, an eDiscovery solution capable of working at a high speed and top-of-the-line accuracy will equip you to fight your cases with maximum efficiency.
Reaping the Benefits Out of Cloud-Based Discovery Software
You can also lose control of your data in expensive cloud platforms. You’re completely dependent on THEIR solution, as they hold your data hostage indefinitely, at whatever rates they set. Plus, if an eDiscovery solution doesn’t have the capacity to scale with your ever-increasing data needs or carry the solutions you need, you can suffer from ineffective workflow functionality.
Your organization needs an eDiscovery solution that provides you with:
- A great degree of workflow flexibility with on-premise and cloud solutions
- The ability to add new fields, as needed
- The power to flex up and down the data storage as you consume, allowing you to only pay for what you need
- The process of continuous improvement in regards to their data processing engine
With a cloud-based eDiscovery solution capable of handling the volume and variety of data you have in addition to the functionality and features you need, you will be able to work efficiently.

Evaluating The CloudNine Explore Solution
As the industry leader for processing eDiscovery data, CloudNine Explore is based on four key components:
- Explore
- Assess
- Protect
- Deliver
Explore:
CloudNine Explore helps you navigate your way through massive volumes of data to identify risk, determine the scope of the project and control your costs. This helps you uncover important information about the data before you begin:
- How much data is there?
- What type of data has been collected?
- What languages are included in the data?
- What data is hidden from view?
- Where did the data come from?
Knowing this information will help you evaluate the risk and potential cost of litigation at the earliest possible point. This knowledge enables you to set more realistic costs to process and store the data, as well as to determine the size of your review team and necessary skill sets.
Assess:
With CloudNine Explore, you can inspect and review your data using both automated and manual processes. When you receive hundreds of thousands of documents and files through eDiscovery, you need to be able to process through it quickly and efficiently. CloudNine Explore’s multi-threaded, multi-core indexing functionality helps you filter through your exported data faster so you can pull only the data you need.
Being thoughtful about your research and using specific keyword search terms to promote specific documents, helps you filter out data like specific email domain names for later review.
Protect:
If the integrity of your data is compromised, lost, distorted or manipulated, the consequence can be devastating to your case.
CloudNine Explore allows you to securely upload, ingest and preserve all relevant data for your ongoing investigations or litigation with an easier and more efficient eDiscovery platform.
All your data is stored securely in a single, on-prem location, housed safely behind the firewall. This safety net saves money while giving you direct access to your data so you know exactly where it is at all times.
Deliver:
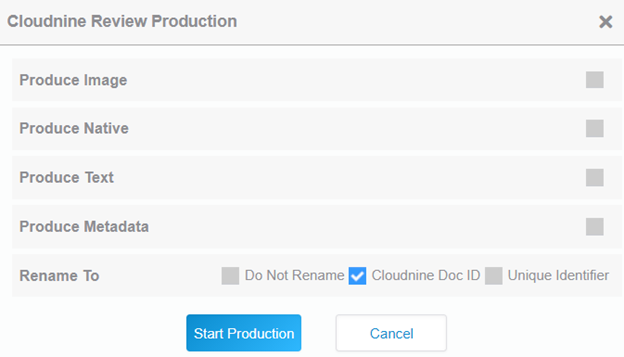
Sharing discovered assets with the opposing side for review is more than a courtesy, it’s required. CloudNine Explore makes it easy to provide information as required for legal production or further investigation so you stay compliant.
Avoid costly and time-consuming production of redundant and unnecessary documents while reducing the risk of producing privileged or protected content.
Faster Data Ingestion, Faster ROI With CloudNine Explore
CloudNine Explore saves you money, which in turn positions your project to yield high ROI.
- Explore works extremely fast, which means less time spent processing and reviewing data.
- Explore stores your data securely in a single, on-prem location, which provides your organization with consistent and transparent pricing.
- Integration costs are minimal because of its simplicity. Installation, scale, and automation are simple and straightforward. You don’t even need an IT department to deploy it.
Now that you’ve learned how CloudNine Explore allows you to safely store and process your data; request a free demo to learn how you can save time and money.












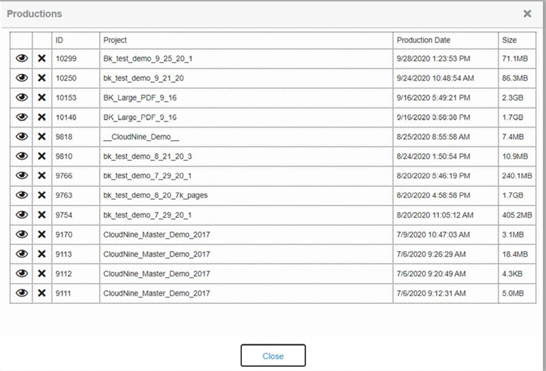
 Document production sizes can range from one document to tens or even hundreds of thousands of documents.
Document production sizes can range from one document to tens or even hundreds of thousands of documents.